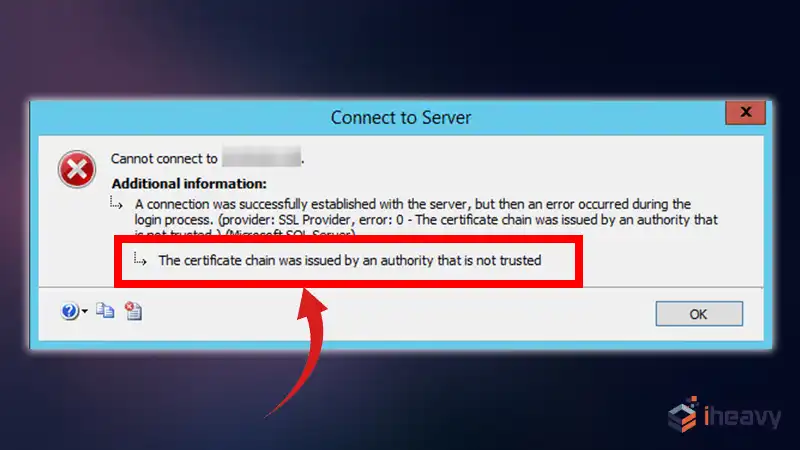
The Certificate Chain Was Issued by an Authority That Is Not Trusted
When working with secure communications, such as HTTPS, SSL/TLS certificates are critical for establishing trust between clients and servers. One common error encountered during this process is “The certificate chain was issued by an authority that is not trusted.”
This error indicates that the certificate presented by the server, or one of the certificates in its chain, is not trusted by the client. In this article, we will explore the causes of this error, how to diagnose it, and various strategies to resolve it.
Understanding the Error
The error message “The certificate chain was issued by an authority that is not trusted” typically occurs because the certificate authority (CA) that issued the server’s certificate is not recognized as a trusted CA by the client.
This can happen for several reasons, such as the certificate being self-signed, the CA not being included in the client’s trusted store, or the chain of trust being incomplete.
Common Causes of the Error
Self-Signed Certificate
A self-signed certificate is one that is not issued by a recognized CA. While useful for testing and development, self-signed certificates are not trusted by default.
Self-signed certificates are not included in the client’s list of trusted CAs.
Missing Intermediate Certificates
If the server’s certificate chain includes intermediate certificates that are not provided during the SSL handshake, the client cannot verify the chain up to a trusted root CA.
Intermediate certificates need to be included in the server’s certificate chain.
Untrusted Root CA
If the root CA that issued the certificate is not trusted by the client’s system, the entire certificate chain will be considered untrusted.
The root CA must be in the client’s trusted store.
Expired or Revoked Certificates
Certificates that have expired or been revoked by the CA will not be trusted by the client.
Ensure that all certificates in the chain are valid and not expired.
How to Resolve the Error
Use a Trusted Certificate Authority
Obtain your SSL/TLS certificates from a trusted CA. These authorities are already included in the trusted stores of most operating systems and browsers.
Use certificates from trusted CAs like Let’s Encrypt, Comodo, or DigiCert.
Include Intermediate Certificates
Ensure that all intermediate certificates are included in the server’s certificate chain. This can typically be done by concatenating the server certificate and intermediate certificates into a single file.
Include intermediate certificates in the server’s certificate chain.
Update the Client’s Trusted Store
If you are using a self-signed certificate or a root CA that is not recognized, you can manually add the certificate to the client’s trusted store.
On Windows:
1. Open the Microsoft Management Console (MMC).
2. Add the Certificates snap-in.
3. Import the certificate into the Trusted Root Certification Authorities store.
On Linux:
# Add the certificate to the trusted store
sudo cp your_certificate.crt /usr/local/share/ca-certificates/
sudo update-ca-certificates
Renew Expired Certificates
Regularly monitor and renew your certificates before they expire to ensure they remain trusted.
Keep track of certificate expiry dates and renew them promptly.
Example Code
Here is an example of how to include intermediate certificates in an Nginx configuration:
server {
listen 443 ssl;
server_name example.com;
ssl_certificate /path/to/your/fullchain.pem; # Concatenated server and intermediate certificates
ssl_certificate_key /path/to/your/private.key;
}Frequently Asked Questions
What is a self-signed certificate?
A self-signed certificate is a certificate that is signed by the entity it certifies, rather than by a trusted CA. Self-signed certificates are generally not trusted by default because they do not provide a chain of trust.
How do I check if my certificate chain is complete?
You can use tools like SSL Labs’ SSL Test or the openssl command-line tool to check your certificate chain. These tools will indicate if any intermediate certificates are missing or if there are any issues with the chain.
Can I use self-signed certificates in production?
Self-signed certificates are not recommended for production environments because they are not trusted by default and can lead to security warnings. It is better to use certificates from a trusted CA for production.
Conclusion
Encountering the error “The certificate chain was issued by an authority that is not trusted” can be a common hurdle when working with SSL/TLS certificates. By understanding the causes and implementing the solutions outlined in this article, you can ensure that your secure communications are trusted and free from certificate validation issues. Whether you are using a self-signed certificate for development or deploying a trusted certificate for production, following best practices will help maintain a secure and reliable system.