Enabling xp_cmdshell in SQL Server
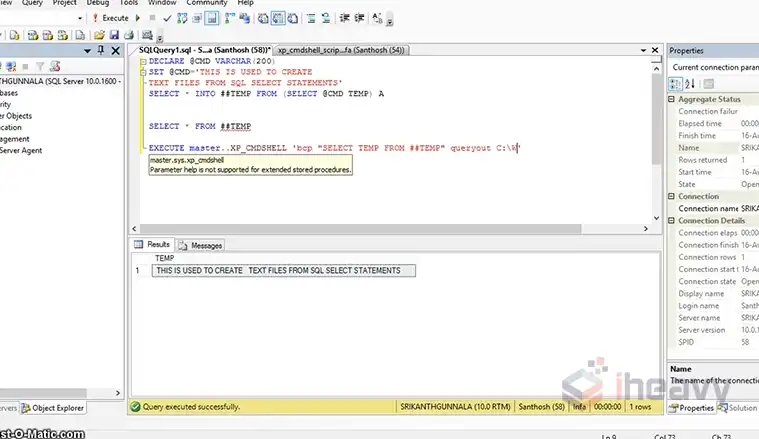
Enabling xp_cmdshell in SQL Server allows users to execute operating system commands directly from SQL Server. This feature is powerful but comes with potential security risks. By default, xp_cmdshell is disabled to prevent unauthorized access to system resources. However, in certain scenarios, such as automated database management tasks or integrating SQL Server with external applications,…