Redshift Schema Permissions | Explained
Amazon Redshift is a fully managed, petabyte-scale data warehouse service in the cloud. One essential aspect of managing a Redshift data warehouse is handling schema permissions. Schemas in Redshift are like containers that hold database objects such as tables, views, and other objects. Properly managing schema permissions ensures that users have the appropriate access to these objects, which is crucial for both security and efficient data management.
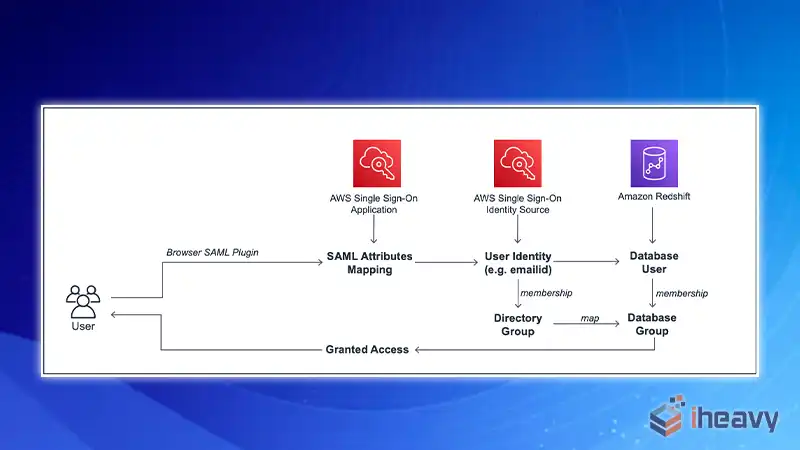
Understanding Schema Permissions in Redshift
In Amazon Redshift, permissions on schemas can be managed using GRANT and REVOKE statements. These permissions determine what actions a user can perform on the objects within a schema.
Types of Permissions
CREATE
Allows users to create objects within the schema.
USAGE
Allows users to access objects within the schema, but does not allow creation of new objects.
ALL
Grants all available permissions on the schema.
Managing Schema Permissions | Granting Permissions
Granting USAGE Permission
To allow a user to access objects within a schema without giving them the ability to create new objects, use the following command:
GRANT USAGE ON SCHEMA schema_name TO user_name;Granting CREATE Permission
To allow a user to create objects within a schema, use the following command:
GRANT CREATE ON SCHEMA schema_name TO user_name;Granting ALL Permissions
To grant all permissions (both USAGE and CREATE) to a user on a schema, use the following command:
GRANT ALL ON SCHEMA schema_name TO user_name;Managing Schema Permissions | Revoking Permissions
Revoking USAGE Permission
To revoke USAGE permission from a user on a schema, use the following command:
REVOKE USAGE ON SCHEMA schema_name FROM user_name;Revoking CREATE Permission
To revoke CREATE permission from a user on a schema, use the following command:
REVOKE CREATE ON SCHEMA schema_name FROM user_name;Revoking ALL Permissions
To revoke all permissions from a user on a schema, use the following command:
REVOKE ALL ON SCHEMA schema_name FROM user_name;Managing Schema Permissions |Viewing Permissions
To view the current permissions on a schema, you can query the pg_namespace and pg_roles system catalog tables.
SELECT nspname, rolname, nspacl
FROM pg_namespace
JOIN pg_roles ON pg_namespace.nspowner = pg_roles.oid
WHERE nspname = 'schema_name';Practical Examples
Example 1 Granting Permissions
-- Grant USAGE and CREATE permissions on the schema 'sales' to the user 'analyst'
GRANT USAGE, CREATE ON SCHEMA sales TO analyst;
-- Grant ALL permissions on the schema 'marketing' to the user 'manager'
GRANT ALL ON SCHEMA marketing TO manager;Example 2 Revoking Permissions
-- Revoke CREATE permission on the schema 'sales' from the user 'analyst'
REVOKE CREATE ON SCHEMA sales FROM analyst;
-- Revoke all permissions on the schema 'marketing' from the user 'manager'
REVOKE ALL ON SCHEMA marketing FROM manager;Frequently Asked Questions
How can I grant a user permission to only read data from a schema in Redshift?
To allow a user to only read data, you should grant them USAGE permission on the schema and SELECT permission on the individual tables within that schema.
GRANT USAGE ON SCHEMA schema_name TO user_name;
GRANT SELECT ON ALL TABLES IN SCHEMA schema_name TO user_name;Can I grant schema permissions to a group of users in Redshift?
Yes, you can grant permissions to a group (role) instead of individual users. First, create the group, add users to it, and then grant permissions to the group.
-- Create a group
CREATE GROUP group_name;
-- Add users to the group
ALTER GROUP group_name ADD USER user1, user2;
--- Grant permissions to the group
GRANT USAGE ON SCHEMA schema_name TO GROUP group_name;How do I check which users have permissions on a schema?
You can query the system catalog tables pg_namespace, pg_roles, and pg_user to see which users have permissions on a schema.
SELECT nspname, usename, nspacl
FROM pg_namespace
JOIN pg_user ON nspowner = usesysid
WHERE nspname = 'schema_name';Conclusion
Properly managing schema permissions in Amazon Redshift is crucial for maintaining data security and ensuring that users have the appropriate level of access to perform their tasks. By using the GRANT and REVOKE statements, you can precisely control what actions users can perform on the objects within a schema. Understanding and applying these permissions effectively can help you manage your Redshift data warehouse more efficiently.