The Complete Azure Security Checklist
As businesses increasingly rely on cloud infrastructure, ensuring the security of your Azure environment is no longer an option but a necessity. A data breach can lead to significant financial losses, reputational damage, and legal repercussions. To safeguard your valuable assets, a comprehensive Azure security checklist is indispensable.
The subsequent sections will delve into the critical areas of Azure security, providing actionable recommendations and best practices. Let’s embark on a journey to protect your Azure infrastructure and data.
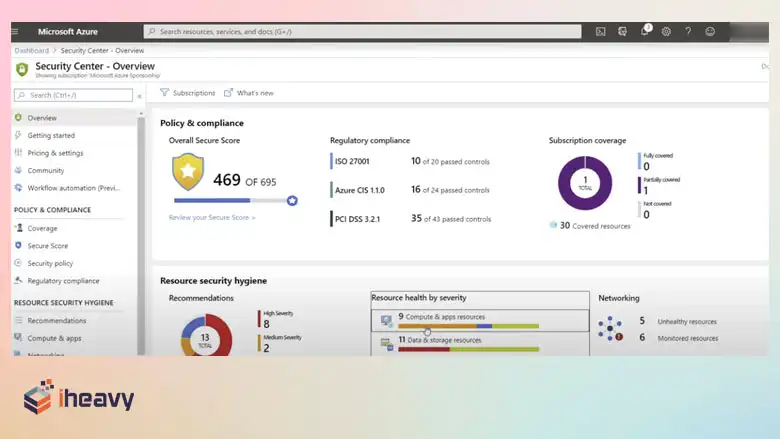
Importance of an Azure Security Checklist
An Azure security checklist serves as a roadmap to identify potential vulnerabilities and implement protective measures. It helps organizations:
- Proactively mitigate risks: By systematically addressing security controls.
- Comply with industry regulations: Ensuring adherence to standards like GDPR, HIPAA, and PCI DSS.
- Build trust with customers: Demonstrating a commitment to data protection.
- Reduce the impact of security incidents: Through effective incident response planning.
Azure Security: Key Areas of Focus
This section will delve into the fundamental components of a comprehensive security strategy. We will explore how to safeguard your identity and access management, protect your sensitive data, secure your network infrastructure, bolster application security, and fortify your overall infrastructure.
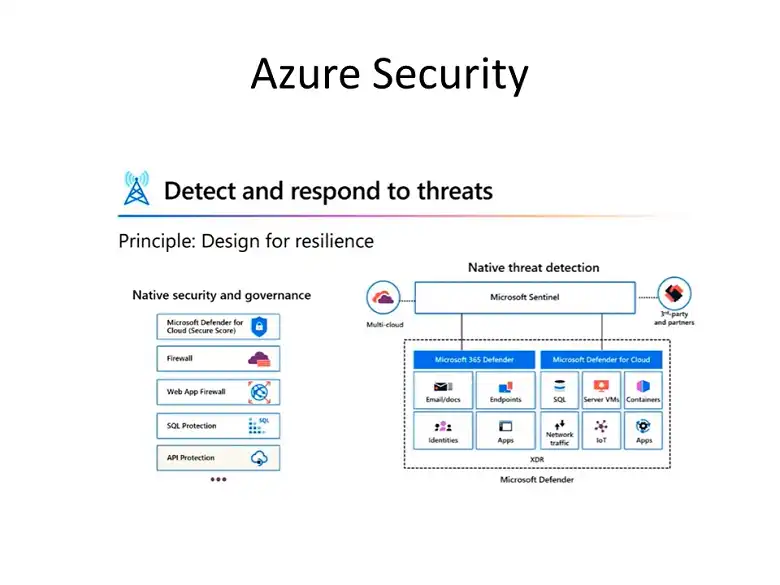
Identity and Access Management (IAM)
Controlling who can access your Azure resources is paramount. Effective IAM ensures that only authorized individuals have the necessary permissions to perform their job functions. Here are some key factors to consider:
- Centralized Identity Management: Utilize Azure Active Directory (Azure AD) for user management and authentication.
- Strong Authentication: Enforce multi-factor authentication (MFA) for all users and administrative accounts.
- Privileged Identity Management (PIM): Implement PIM to control administrative access and require just-in-time (JIT) elevation.
- Access Reviews: Regularly review and clean up user accounts and permissions.
- Least Privilege Principle: Grant users only the necessary permissions to perform their job functions.
Data Protection
Protecting your organization’s sensitive data is paramount. This section outlines strategies to safeguard information at rest, in transit, and in use.
Data Classification: Categorize data based on sensitivity to determine appropriate protection levels.
Data Encryption: Encrypt data at rest and in transit using Azure’s built-in encryption capabilities.
Key Management: Manage encryption keys securely using Azure Key Vault.
Data Loss Prevention (DLP): Implement DLP policies to protect sensitive information.
Backup and Recovery: Regularly back up data and test recovery processes.
Network Security
Your Azure network is the digital backbone of your operations. Safeguarding it is crucial to prevent unauthorized access, data breaches, and service disruptions. This section explores strategies to fortify your network perimeter, protect data in transit, and detect and respond to potential threats.
- Network Segmentation: Isolate network resources using virtual networks and subnets.
- Network Security Groups (NSGs): Configure NSGs to control inbound and outbound network traffic.
- Azure Firewall: Deploy Azure Firewall for advanced threat protection and application filtering.
- Virtual Network Peering: Securely connect virtual networks when necessary.
- Intrusion Detection and Prevention Systems (IDPS): Utilize Azure Security Center for threat detection.
Application Security
Secure Development Lifecycle (SDLC): Integrate security into the development process.
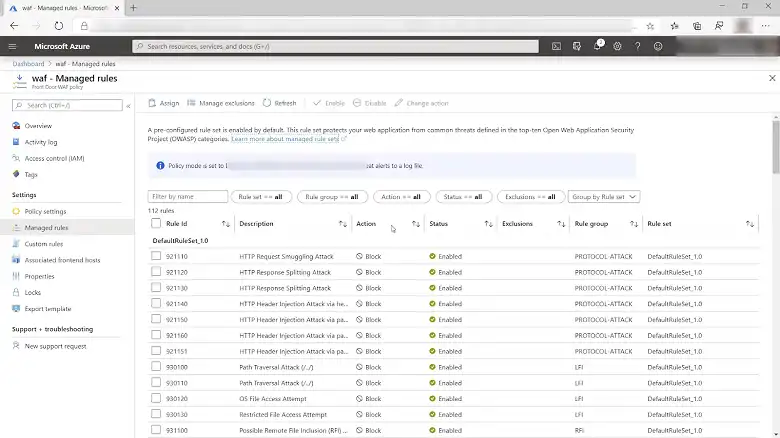
Web Application Firewall (WAF): A Web Application Firewall (WAF) is an essential security tool that acts as a shield, protecting your web applications from a variety of attacks. It sits between your web application and the internet, scrutinizing incoming and outgoing traffic for malicious activity.
By implementing a WAF, you can safeguard your applications against common threats like:
- SQL injection: Prevents malicious code from being injected into databases.
- Cross-site scripting (XSS): Protects against malicious scripts injected into web pages.
- Cross-site request forgery (CSRF): Defends against unauthorized actions performed on behalf of a legitimate user.
- Other vulnerabilities: Protects against a wide range of application-layer attacks.
WAFs can operate in different modes, such as positive security (whitelist) or negative security (blacklist), allowing you to customize protection based on your specific needs. By integrating a WAF into your application security strategy, you can significantly reduce the risk of data breaches and maintain the integrity of your web applications.
Vulnerability Assessment: Regularly scan applications for vulnerabilities.
Secure Coding Practices: Adhere to secure coding standards and guidelines.
Input Validation: Validate and sanitize user input to prevent injection attacks.
Infrastructure Security
Patch Management: Keep operating systems and applications up-to-date with patches.
Virtual Machine Security: Harden virtual machines with security best practices.
Secure Storage: Protect data stored in Azure Storage accounts.
Monitoring and Logging: Implement comprehensive monitoring and logging solutions.
Incident Response Planning: Develop and test an incident response plan.
Azure Security Checklist
To provide a structured approach to implementing security controls, we’ve created a comprehensive Azure security checklist. The following table outlines key areas and corresponding control measures.
| Area | Control | Description |
| Identity and Access Management | Centralized Identity Management | Use Azure AD for user management |
| Identity and Access Management | Strong Authentication | Enforce MFA for all users |
| Identity and Access Management | Privileged Identity Management | Implement PIM for administrative access |
| Data Protection | Data Classification | Categorize data based on sensitivity |
| Data Protection | Data Encryption | Encrypt data at rest and in transit |
| Network Security | Network Segmentation | Isolate network resources using virtual networks |
| Network Security | NSGs | Configure NSGs to control network traffic |
| Application Security | Secure Development Lifecycle | Integrate security into development |
| Infrastructure Security | Patch Management | Keep systems and applications up-to-date |
Note: This table provides a basic overview. A comprehensive checklist should include more granular controls and specific recommendations based on your organization’s risk profile.
Additional Security Considerations
Beyond the core security controls outlined above, several additional measures can significantly enhance your Azure environment’s protection.
- Azure Security Center: Leverage Azure Security Center for centralized security management and threat detection.
- Compliance Standards: Assess your organization’s compliance requirements and implement necessary controls.
- Security Awareness Training: Educate employees about security best practices.
- Regular Security Assessments: Conduct vulnerability assessments and penetration testing.
- Continuous Monitoring: Monitor your Azure environment for threats and anomalies.
Frequently Asked Questions
What is the difference between Azure Security Center and Azure Monitor?
Azure Security Center focuses on security-related threats and vulnerabilities, while Azure Monitor provides a broader view of the overall health of your Azure environment.
How often should I review my Azure security checklist?
It’s recommended to review your checklist at least annually or whenever there are significant changes to your environment.
Can I use third-party security tools in addition to Azure native services?
Yes, you can complement Azure’s built-in security features with third-party solutions to address specific needs.
Conclusion
This in-depth guide offers a step-by-step approach to fortifying your Azure environment against potential threats. By following the outlined security measures, you can significantly reduce your organization’s risk exposure, comply with industry regulations, and build trust with customers.
Remember, security is an ongoing process. We encourage you to adapt and refine your security measures as the threat landscape evolves.