SQL Server Encryption Best Practices
SQL Server encryption plays a crucial role in safeguarding sensitive data against unauthorized access and potential breaches. Properly implemented encryption ensures that even if data is intercepted, it remains unreadable without the correct decryption keys.
To maintain data security and compliance with regulatory standards, it is important to follow best practices when encrypting data in SQL Server. This article covers essential techniques and strategies to optimize encryption in SQL Server.
What Encryption Is Used in SQL Server?
SQL Server offers various encryption methods, each serving a specific purpose. Before implementing encryption, it’s crucial to understand these methods:
Transparent Data Encryption (TDE)
TDE encrypts the data files and log files, ensuring that data is protected at rest without requiring any changes to the application accessing the data. This type of encryption is particularly useful for safeguarding databases from physical theft, such as the theft of storage media.
TDE is implemented by encrypting the database with a database encryption key (DEK), which is stored in the database boot record and secured by a certificate or an asymmetric key stored in the master database. However, it does not encrypt data within the memory or in transit.
Column-Level Encryption
When specific columns within a table contain sensitive information, column-level encryption is a more granular approach. This method involves encrypting data at the column level using symmetric or asymmetric keys.
Unlike TDE, column-level encryption allows for more control over which data is encrypted and is especially useful for protecting highly sensitive information like social security numbers or credit card details. However, it may require changes to the application code to handle encryption and decryption processes.

Encrypting File System (EFS)
You can also encrypt data at the file system level using Windows EFS. This method is useful for encrypting SQL Server backups and other files.
Transport Layer Security (TLS)
TLS ensures that data transmitted between SQL Server and client applications is encrypted. It protects against man-in-the-middle attacks and unauthorized data interception.
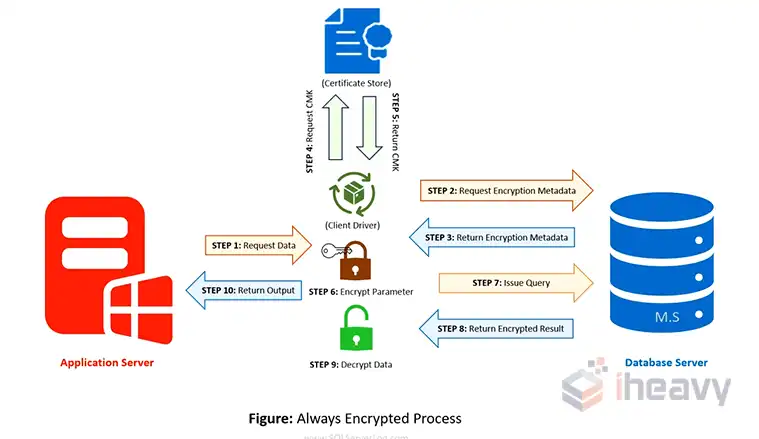
What Is Always Encrypted in SQL Server?
Always Encrypted is designed to protect sensitive data, such as credit card numbers or national identification numbers, stored in SQL Server databases. Unlike other encryption methods, Always Encrypted ensures that the data is encrypted both at rest and in use.
Encryption and decryption occur on the client side, using keys stored outside SQL Server. This method prevents database administrators from viewing sensitive data while allowing applications to handle encrypted data transparently.
What Are SQL Server Encryption Best Practices?
Below are some guidelines and recommendations for implementing effective encryption strategies within your SQL Server environment.
1. Use Strong Encryption Algorithms
When configuring encryption, it’s essential to use strong encryption algorithms. SQL Server supports several algorithms, but not all offer the same level of security. For optimal protection:
- Prefer AES_256 over weaker algorithms like DES or RC4. AES_256 provides a higher security level and is recommended for most encryption needs.
- Regularly review and update encryption algorithms to stay current with evolving security standards. What is considered secure today may not be tomorrow.
2. Implement Key Management Best Practices
Encryption keys are the cornerstone of any encryption strategy. Proper management of these keys is crucial to maintaining data security:
Separate Key Storage: Store encryption keys separately from the encrypted data. This reduces the risk of both being compromised simultaneously.
Use SQL Server’s Extensible Key Management (EKM): EKM allows integration with third-party hardware security modules (HSMs) to enhance key management capabilities.
Rotate Encryption Keys Regularly: Periodic key rotation limits exposure in case of a key compromise. Implement a robust key rotation policy that aligns with your organization’s security policies.
Backup Keys Securely: Always maintain secure backups of encryption keys. Losing keys means losing access to your data, so it’s vital to have reliable and secure backup processes in place.

3. Encrypt Sensitive Data at the Column Level
For data that is highly sensitive, such as Personally Identifiable Information (PII), consider using column-level encryption. This method offers granular control over what data is encrypted, allowing you to encrypt only the most sensitive information:
- Evaluate which columns need encryption based on the sensitivity of the data they contain.

- Use deterministic encryption for columns that require indexing, searching, or joining with other tables. However, keep in mind that deterministic encryption can be less secure than random encryption because it can produce the same encrypted output for identical inputs.

4. Enable Transparent Data Encryption (TDE) for Databases
Transparent Data Encryption (TDE) provides an effective way to protect data at rest with minimal changes to applications. Enabling TDE is straightforward:
1. Create a Database Master Key:
CREATE MASTER KEY ENCRYPTION BY PASSWORD = 'YourStrongPassword';This key is necessary for encrypting the certificates used by TDE.

2. Create a Certificate:
CREATE CERTIFICATE TDECert WITH SUBJECT = 'TDE Certificate';3. Enable TDE on the Database:
USE YourDatabaseName;
CREATE DATABASE ENCRYPTION KEY WITH ALGORITHM = AES_256 ENCRYPTION BY SERVER CERTIFICATE TDECert;
ALTER DATABASE YourDatabaseName SET ENCRYPTION ON;By following these steps, you can easily encrypt an entire database, ensuring that data at rest is protected.
5. Encrypt Backups and Utilize Secure Storage Solutions
Encrypting backups is as crucial as encrypting active databases. Backups are a prime target for attackers because they often contain full copies of the database.
- Use Backup Encryption to encrypt backups using the same or different certificates from the primary database.
- Store backups in secure locations, such as encrypted cloud storage or on-premises locations with limited access.
6. Ensure Transport Layer Security (TLS) for Data in Transit
To protect data as it travels between the SQL Server and clients, use TLS:
Configure SQL Server to Force Encryption: This ensures that all communications are encrypted, preventing data from being intercepted during transit.
EXEC sp_configure 'show advanced options', 1;
RECONFIGURE;
EXEC sp_configure 'force encryption', 1;
RECONFIGURE;Use the Latest TLS Versions: Regularly update to the latest TLS version to mitigate vulnerabilities found in older versions. Disable older, less secure protocols like SSL or early versions of TLS.
7. Regularly Audit and Monitor Encryption Practices
Even the best encryption strategies need regular auditing and monitoring to remain effective:
Perform Regular Audits: Check that all sensitive data is encrypted and that encryption policies are being followed. Regular audits help identify potential gaps in encryption coverage or areas for improvement.
Monitor for Unauthorized Access: Use SQL Server’s auditing features to monitor access to encrypted data and encryption keys. Detecting unauthorized access attempts can provide early warning of potential security breaches.
8. Stay Updated on Encryption Vulnerabilities and Best Practices
Encryption technologies and practices evolve, and staying informed about the latest threats and best practices is vital:
- Subscribe to security bulletins and alerts from SQL Server and encryption technology providers.
- Regularly review and update your encryption strategy to align with the latest security recommendations and standards.
Frequently Asked Questions
Does SQL Server encrypt data at rest?
Transparent Data Encryption (TDE) safeguards SQL Server, Azure SQL Database, and Azure Synapse Analytics data files by encrypting them at rest. To bolster the security of your user database, consider implementing strategies such as: Designing a robust and secure system architecture.
How do I know if SQL Server is encrypted?
The ‘dm_database_encryption_keys’ query shows the encryption status of all databases on your SQL Server instance. The ‘encryption_state’ column reveals whether Transparent Data Encryption (TDE) is enabled for each database. A value of 3 in the ‘encryption_state’ column signifies that TDE is active.
Does SQL Server support AES encryption?
SQL Server employs the Advanced Encryption Standard (AES) algorithm to safeguard the service master key (SMK) and the database master key (DMK). AES is a more modern encryption algorithm compared to 3DES, which was used in previous versions of SQL Server.
Conclusion
Implementing SQL Server encryption best practices is critical to safeguarding your data against unauthorized access and breaches. By understanding the different encryption options, using strong algorithms, managing encryption keys effectively, and continuously auditing and updating your encryption practices, you can ensure that your data remains secure.